What Is ARP? Address Resolution Protocol Explained
Address Resolution Protocol (ARP) is a protocol used to resolve IP addresses to MAC addresses. Without ARP, devices wouldn't be able to communicate with each other, making it an essential part of modern computer networks. In this article, learn what ARP is, how arping works, and why the protocol is essential for network communication.
What is ARP?
ARP stands for Address Resolution Protocol. This network protocol maps IP addresses to Media Access Control (MAC) addresses in local area networks. Essentially, the primary duty of the Address Resolution Protocol is to translate 32-bit IP addresses into 48-bit MAC addresses, which is vital for two devices to properly communicate and share information.
Every device within a network has two addresses: an IP address and a MAC address. While your IP address changes, your MAC address is static and does not change. Therefore, ARP is what keeps these two systems connected.
Address Resolution Protocol is like a translator for Internet addresses. When your router assigns an IP address to your phone, computer, or other connected device, the protocol matches that IP address to the MAC address so that the information arrives at the right place.
Address Resolution Protocol is found in the data link layer of the OSI model. The data link layer is responsible for the communication between devices on the same local network. The protocol operates at this layer to resolve the mapping between IP addresses, which are layer 3 addresses, and MAC addresses, which are layer 2 addresses.
Though Address Resolution Protocol is fast and efficient, it is vulnerable to ARP spoofing attacks and ARP poisoning. In incidents like these, malicious actors can manipulate and damage the system.
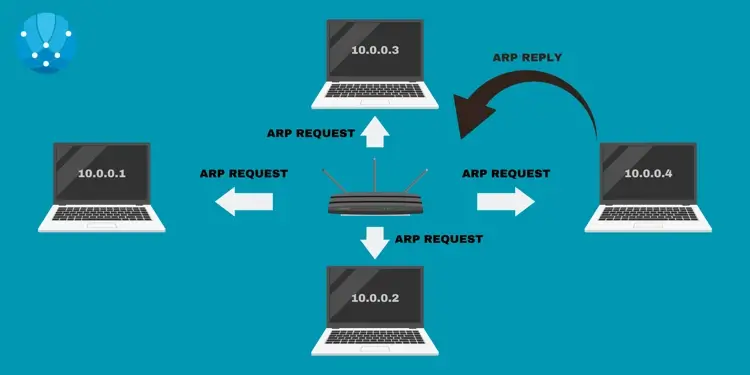
How ARP works
Address Resolution Protocol is like an automated phone book for IP addresses. It works by broadcasting a request packet on the network that essentially asks who has a certain IP address. The device with that IP address will then respond with its MAC address.
Now, the requesting device knows the IP and corresponding MAC address and stores them in the ARP cache for future use.
When the source computer wants to communicate with the target computer, it follows a process. First, the source computer checks its ARP cache to see if it already knows the target computer's MAC address. If it does, it sends the data immediately. If it doesn't have the MAC address, the source computer sends an Address Resolution Protocol request broadcast onto the network, asking for the target computer's MAC address.
The target computer then sees the request and responds with its MAC address. The source computer stores the IP-MAC address pair in its ARP cache and sends the data to the target computer.
Then, the next time the source computer needs to communicate with the target computer, it will already have the information in its ARP cache and can send the data right away.
Essentially, the ARP protocol is fundamental to how IP-based networks operate. It ensures that communication at layer 3 is delivered to layer 2, where MAC addresses are used. Without ARP, our networks won't be able to match logical IP addresses to handle physical hardware addresses.
What is arping?
Arping is a command-line network utility used to send requests to a specific IP address. The aim of arping is to determine whether a specific IP address on a local network is in use or available.
Arping is similar to the ping command, as both check the status of IP addresses within a local network. However, the ping command operates at the network layer, whereas arping operates at the data link layer.
Arping can be helpful in scenarios where you want to:
- Troubleshoot IP address conflicts
- Troubleshoot Address Resolution Protocol problems, like gratuitous Address Resolution Protocol replies or poisoning attacks
- Determine the MAC address of a device given its IP address
- Verify the connectivity of a particular IP address
- Verify that a device is available and responsive
- Probe hosts on a LAN to determine their operating system
- Identify rogue devices on a network
Arping is available on most Unix operating systems, including Linux and MacOS.
Consider the command arping -c 3 192.168.1.190. In this example, arping receives instruction to send a single ARP request to the device with the IP address 192.168.1.1 and report back any responses. If the device is available, it will respond with its MAC address.
Understanding ARP packet structure
The ARP packet format is useful for ARP requests and replies because it contains several fields that facilitate IP to MAC translation. These include:
- Hardware type, which indicates the type of hardware (like Ethernet)
- Protocol type, which specifies the protocol (like IPv4)
- Hardware address length, which indicates the length of the MAC address
- Protocol address length, which indicates the length of the IP address
- Opcode, which is the operation code, such as ARP request (1) or ARP reply (2)
- Sender hardware address, which is the MAC address of the sender
- Sender protocol address, which is the IP address of the sender
- Target hardware address, which is the MAC address of the target
- Target protocol address, which is the IP address of the target
All of these fields are included in the ARP packet sent across the network.
ARP cache entries
The ARP cache is simply a table that stores the mapping of IP addresses to their corresponding MAC addresses. It allows devices to communicate directly without broadcasting protocol requests for every packet sent. But ARP cache entries eventually time out, typically after a few minutes.
When an entry times out, the device will have to broadcast another ARP request the next time it needs to send a packet to that IP address. This helps ensure that the ARP cache contains the most up-to-date MAC address mappings.
Each entry in the ARP cache includes:
- the IP address
- the MAC address
- the interface through which the MAC address can be reached
- a timestamp for entry updates
You can view your device's cache using a command like arp -a on Linux or arp -g on Windows. This shows you all of the current IP to MAC mappings that your device knows about.
How is the Address Resolution Protocol cache updated?
The Address Resolution Protocol cache updates in a few ways. First, when a request is broadcasted and a response is received, the cache updates with the new IP to MAC information. Additionally, when a device receives a packet from an IP address not currently in its ARP cache, it broadcasts a request and updates its cache with the response.
Periodically, devices will re-ARP for devices in their cache to ensure the information is still up to date before the entry times out. You can also manually add or delete entries in the cache using arp commands like arp -s to add a static entry or arp -d to delete an entry. All of these processes update the protocol cache.
Types of Address Resolution Protocol entries
There are two types of entries: static entries and dynamic entries. You'll likely use dynamic entries more often, but read below to understand the difference between the two.
Static entries
Static ARP entries are manually created and mapped by a network administrator. They provide a permanent mapping between an IP address and a MAC address. Static Address Resolution Protocol entries don't change unless the administrator updates them.
Static Address Resolution Protocol provides a consistent mapping for critical network devices like routers, switches, or servers. It also prevents ARP poisoning attacks by locking in the correct MAC address to IP address mapping and ensures connectivity for devices that may not respond to ARP requests, like printers or IoT devices.
The downside to static entries is that they require manual configuration. The maintenance, especially for large networks, can be time consuming.
Dynamic entries
Dynamic ARP entries are created automatically through the Address Resolution Protocol process. When a device sends out a request, the device that owns the IP address responds with its MAC address. This creates a dynamic Address Resolution Protocol entry that maps the IP and MAC.
The entries are temporary and age out after a set period if unused. Dynamic Address Resolution Protocol requires no manual configuration, but the mappings can change, which may disrupt connectivity. The entry is ideal for standard network devices like workstations, laptops, tablets, and phones.
Common ARP commands
We use Address Resolution Protocol commands to view, display, or modify the protocol cache on our computer. You can run a few useful commands to troubleshoot connectivity issues or view ARP cache information.
They include:
- arp -a: Displays the current ARP cache, which shows IP addresses mapped to MAC addresses. This therefore allows you to see the ARP entries for the local network.
- arp -s: Allows you to add a static ARP entry. You specify the IP and MAC addresses, and the entry is added to the ARP cache. Static entries don't time out; instead, they persist until removed.
- arp -d: Deletes an ARP entry. You specify the IP address you want to remove, and the corresponding cache entry is then deleted.
- arping: Sends Address Resolution Protocol requests to a specified IP address. This allows you to query a device's MAC address or test if an IP address is reachable.
- arp purge-delay: This command delays the purging of Address Resolution Protocol entries in a table when the interface slows or goes down.
- proxy-arp: This is responsible for enabling the proxy on an interface. The network devices can respond to requests only when the proxy is enabled.
- no proxy-arp: This command disables the proxy-arp on the interface.
- show arp: This indicates the Address Resolution Protocol.
By understanding how to use ARP commands, you'll better equip yourself to diagnose network communication issues.
What are the types of Address Resolution Protocol?
Several types of Address Resolution Protocol serve specific purposes in network communication. They include the following:
- RARP (Reverse ARP): RARP works in older networks to map MAC addresses to IPv4 addresses. Most systems primarily used it for disk-less workstations to obtain their IP addresses from a server based on their MAC address.
- IARP (Inverse ARP): IARP is an extension of the original protocol that is used in frame relay networks. It lets a device discover the IPv4 address associated with a particular DCLI, or data link connection identifier, in frame relay.
- Proxy ARP: Proxy Address Resolution Protocol is a technique where one device, typically a router, responds to ARP requests on behalf of another device not on the same network segment. IT experts use it for routing purposes.
- Gratuitous ARP: This type of Address Resolution Protocol is a message in which a device announces its own IPv4 to MAC address mapping on the local network. Gratuitous Address Resolution Protocol often updates caches on other devices in the network or detects IP conflicts.
Frequently asked questions
What is ARP spoofing?
ARP spoofing is a malicious cyberattack where an attacker fakes Address Resolution Protocol messages to associate their MAC address with a target's IP address, thus intercepting traffic.
I can't access a device on my network by IP. Could it be an ARP issue?
Yes, it's possible. Try running the arp -a command to view your cache. If the IP address of the unavailable device maps to an incorrect MAC address, then you may need to delete the entry using arp -d and let your computer re-ARP for the correct MAC address.
What are the advantages of Address Resolution Protocol ?
Address Resolution Protocol makes it easy to identify MAC addresses if you know an IP address, so there is no need to configure end nodes to know the MAC addresses.
What are the disadvantages of Address Resolution Protocol ?
Address Resolution Protocol is vulnerable to cyberattacks like spoofing or poisoning. This can also allow hackers to carry out other attacks, such as denial-of-service (DOS) attacks, man-in-the-middle attacks, or session hijacking.